What is IoT? It's about Value
The location, position, and functional state of most “things,” from alarm clocks to cars, including the human body, have been largely hidden or inaccessible for a long time. But this has changed with the Internet of Things (IoT), a set of technologies and related business processes that enable us to track and count, observe and identify, evaluate and act on situations that were previously unseen and out of reach.
When we look at other definitions we also get a picture of the technological interpretation of IoT as a term. According to Wikipedia, IoT is “a network of physical devices, vehicles, appliances and other physical objects that are embedded with sensors, software and network connectivity that allows them to collect and share data.” Meanwhile IBM defines IoT as “a network of physical objects that use a variety of technologies to connect the digital and physical worlds.”
By removing many of the limitations that have traditionally shaped fundamental business processes with these technologies, the IoT requires that we start from rethinking how to create value.
How to create value: The Information-Value Loop
 We have found that the way companies create value has undergone a radical transformation. A person does not value their toothbrush only based on the bristles, the handle, and the battery life, but also, as in the case of Oral-B's Genius X smart toothbrush, on the information it provides about their brushing habits and how to improve them.
We have found that the way companies create value has undergone a radical transformation. A person does not value their toothbrush only based on the bristles, the handle, and the battery life, but also, as in the case of Oral-B's Genius X smart toothbrush, on the information it provides about their brushing habits and how to improve them.
In other words, the value of a product or service is not just determined by its features, but also by the information it offers. And information, creates value in a very different way than products or services do.
By using a smart toothbrush, you can find out how well you brush your teeth. But this is not very useful unless you can change your behavior to achieve your goal of having better oral health. This means that information only adds value when it leads to different and better actions in the future. These actions then produce more information, which enables further learning. So information does not create value in a straight line of steps, but in a continuous value loop.
However, just having information is not enough to use it effectively. We also need to understand the stages between doing something in the world (your brushing) and doing it better (your improved brushing).
To complete a cycle of the Value Loop, from doing to doing better, data is sent from where it is created to where it can be processed, maybe from your smart toothbrush to your smartphone. Data is collected over time or space to form data sets that can be examined and processed to suggest actions. For example:
- Data from one brushing session is not as valuable as data from a whole month
- Data from a whole month is not as motivating as comparing your brushing with others like you
These suggestions help you adjust your brushing. Then new actions are sensed, which create data to make new information, and the cycle starts again.
This is what we will call the Information-Value Loop, a concept we adjusted and expanded to a more practical standpoint based on Deloitte's IoT Information Value Loop.
Defining an Information-Value Loop
We capture the stages through which information passes in order to create value with the Information Value Loop
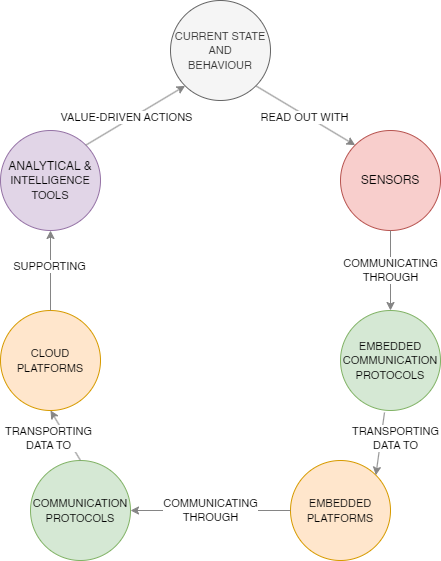
- CREATE : Use of sensors to generate data about a physical event or state
- COMMUNICATE: Transmission of data from generation to processing location using communication protocols at different levels
- AGGREGATE: Gathering data created at different times or from different sources, on platforms, following applicable standards. These platforms can be cloud platforms or (embedded) devices acting as platforms
- ANALYZE: Discernment of patterns amongst data that leads to information, descriptions, predictions or automated actions using analytical and intelligence tools
- ACT: Initiating, changing or maintaining a state or behaviour, be it manually or using actuators. Supported by information these are value-driven actions, actions to create more value
Sensors: Creating
 What allows us to create data from action, state or behaviour is the use of sensors.
What allows us to create data from action, state or behaviour is the use of sensors.
A sensor converts a non-electrical input into an electrical signal that can be sent to an electronic circuit. The Institute of Electrical and Electronics Engineers (IEEE) provides a formal definition:
Institute of Electrical and Electronics Engineers (IEEE) definition of a Sensor
An electronic device that produces electrical, optical, or digital data derived from a physical condition or event. Data produced from sensors is then electronically transformed, by another device, into information (output) that is useful in decision making done by “intelligent” devices or individuals (people).
Sensors can perform different roles and gather various kinds of data. For instance:
- Accelerometers can detect the variation in velocity and direction of an object. They can identify if an object is in motion and which way it is going.
- Temperature sensors can detect the heat and coldness of an object. They can measure the thermal energy and changes in an object's surroundings.
- Humidity sensors can detect the moisture and dryness of an object. They can measure the water vapor and relative humidity in an object's environment.
- Optical sensors can detect the light that an object reflects or emits
- Pressure sensors can detect the force that an object exerts or receives.
By combining multiple sensors, each with a different role, we can create complex systems that create diverse types of data.
It is very important to select the correct type of sensor based on a number of factors and how it can communicaticate the generated data.
Communication protocols: Communicating
Data that sensors create rarely attains its maximum value at the time and place of creation. The signals from sensors often must be communicated to other locations for aggregation and analysis. This typically involves transmitting data over a network. Once devices are connected to a network and they identify each other, communication protocols (a set of rules) provide a common language for devices to communicate.
 Regular wireless or wired communication protocols are used to communicate between devices that are not part of an embedded system, such as computers, smartphones, routers and the Cloud. These protocols are usually more complex, flexible, and secure, as they have to deal with different types of data, networks, and devices. Some examples of non-embedded communication protocols are WiFi, Bluetooth, and USB.
Regular wireless or wired communication protocols are used to communicate between devices that are not part of an embedded system, such as computers, smartphones, routers and the Cloud. These protocols are usually more complex, flexible, and secure, as they have to deal with different types of data, networks, and devices. Some examples of non-embedded communication protocols are WiFi, Bluetooth, and USB.
- WiFi (Wireless Fidelity) is a wireless communication protocol that uses radio waves to transmit data over a local area network (LAN). It supports different standards and frequencies, and provides high-speed data transfer and encryption. It is widely used to connect devices to the Internet or to each other.
- Bluetooth is a wireless communication protocol that uses short-range radio waves to transmit data over a personal area network (PAN). It supports different profiles and versions, and provides low-power data transfer and security. It is commonly used to connect devices such as headphones, speakers, keyboards, and mice to a computer or a smartphone.
- USB (Universal Serial Bus) is a wired communication protocol that uses a standard connector and cable to transmit data and power over a bus. It supports different types and speeds of devices, and provides plug-and-play functionality and security. It is widely used to connect devices such as flash drives, cameras, printers, and chargers to a computer or a power source.
 Embedded communication protocols are used to communicate between devices that are part of an embedded system, such as microcomputers, sensors, and actuators. These protocols are usually simple, fast, and efficient, as they have to operate with limited resources and power consumption. Some examples of embedded communication protocols are I²C, SPI and UART, explained in simple terms for now:
Embedded communication protocols are used to communicate between devices that are part of an embedded system, such as microcomputers, sensors, and actuators. These protocols are usually simple, fast, and efficient, as they have to operate with limited resources and power consumption. Some examples of embedded communication protocols are I²C, SPI and UART, explained in simple terms for now:
- I²C is a way of communicating between parts of an embedded system that only need two wires to connect them. Each device has a name, and they can communicate to each other at different speeds and ways.
- SPI is another way of communicating between parts of an embedded system that need four wires to connect them. One part is the boss, and the others are the workers. They can communicate very fast and at the same time, but they need more wires for more workers.
- UART is a way of communicating between parts of an embedded system that only need one wire to connect them. They don't need a clock to tell them when to communicate, but they need to agree on how fast they communicate. They can communicate both ways or one way at a time.
Platforms: Aggregate
In an IoT setting, sensor and device data can arrive at either embedded platforms or cloud platforms, depending on the source and destination of the data.
For example, a temperature sensor can send data to a Raspberry Pi using an embedded communication protocol, and the Raspberry Pi can send data to a cloud service like AWS or Azure using a regular wireless or wired communication protocol.
Embedded platforms
 Embedded platforms are devices that are part of an embedded system, which can be divided into two categories: microcontroller platforms and microprocessor platforms:
Embedded platforms are devices that are part of an embedded system, which can be divided into two categories: microcontroller platforms and microprocessor platforms:
- Microcontroller platforms are integrated circuits that contain a CPU, memory, and I/O ports on a single chip. They are typically used for simple and low-power applications, such as Arduino or ESP32.
- Microprocessor platforms are devices that have a microprocessor, memory, and I/O ports on a single board and run an operating system like Linux. They are typically used for more complex and high-performance applications, such as Raspberry Pi, BeagleBone, and Jetson Nano.
Embedded platforms can communicate with each other or with external sensors using embedded communication protocols. These protocols are optimized for low power consumption, high reliability, and simple implementation.
(Cloud)platforms
 Cloud platforms are services that provide computing, storage, networking, and other resources over the internet. They can be accessed by any device that has an internet connection, such as laptops, tablets, routers, and the Cloud itself. Cloud platforms can communicate with each other or with embedded platforms using regular wireless or wired communication protocols. These protocols are designed for high bandwidth, scalability, and interoperability.
Cloud platforms are services that provide computing, storage, networking, and other resources over the internet. They can be accessed by any device that has an internet connection, such as laptops, tablets, routers, and the Cloud itself. Cloud platforms can communicate with each other or with embedded platforms using regular wireless or wired communication protocols. These protocols are designed for high bandwidth, scalability, and interoperability.
 Other non-embedded platforms can connect to an embedded platform so that it can send data to that instead, when there is no Cloud platform involved. Information is then just shown on the something like the smartphone itself. In that case this device (like the smartphone) replaces a cloud platform in our information-value loop. This is common in small-scale retail IoT products.
Other non-embedded platforms can connect to an embedded platform so that it can send data to that instead, when there is no Cloud platform involved. Information is then just shown on the something like the smartphone itself. In that case this device (like the smartphone) replaces a cloud platform in our information-value loop. This is common in small-scale retail IoT products.
Data aggregation and processing
 Data gets aggregated and processed following applicable standards on these platforms. Aggregation is the process of gathering data created at different times or from different sources, on platforms.
Data gets aggregated and processed following applicable standards on these platforms. Aggregation is the process of gathering data created at different times or from different sources, on platforms.
These standards can be:
- Technical standards, such as data formats, protocols, and interfaces. For example:
- SQL (Structured Query Language) is a standard language for accessing and manipulating relational databases, which can store structured data from various IoT devices and sensors.
- JSON (JavaScript Object Notation) is a standard format for exchanging data between web services and applications, which can represent semi-structured or unstructured data from various IoT sources.
- Legal and regulatory standards, such as data privacy, security, and ownership. For example:
- GDPR (General Data Protection Regulation) is a standard regulation for data protection and privacy in the European Union, which applies to any IoT data that involves personal information of EU citizens.
- ISO/IEC 27001 is a standard certification for information security management systems, which can help IoT organizations to establish and maintain best practices for data protection and risk management.
- NISTIR 8228 is a standard framework for cybersecurity and privacy risk management for IoT systems, which can help IoT organizations to identify and address potential threats and vulnerabilities in their data lifecycle.
For effective aggregation and use of the data for analysis, there is a need for both types of standards to handle unstructured data and maintain data integrity.
Analytical and intelligence tools: Analyze
Analysis where data is transformed into information and even insights with the help of cognitive technologies and their associated models.
The goal of analysis is to inform action, which is the next stage in the information-value loop. Analytics typically involve sifting through mountains of what is often confusing and conflicting data in search of nuggets of insight that may inform better decisions.
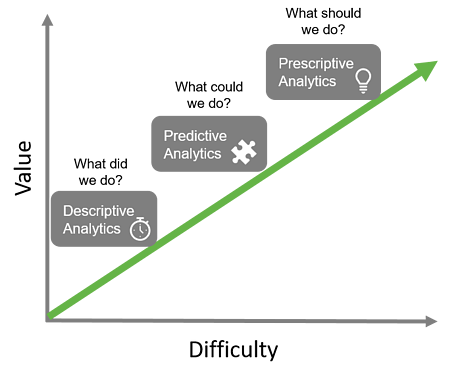
There are three main types of analytical and intelligence tools that can inform action in different ways:
 Descriptive analytics helps us work with large or complex data sets by using tools to answer the question "What did we do?".
Descriptive analytics helps us work with large or complex data sets by using tools to answer the question "What did we do?".These tools include data visualization software such as Tableau and PowerBI, which make data more understandable using charts, graphs and relevant numbers to reveal insights that might otherwise be hidden.
Predictive analytics gives us a deeper insight into what might happen or what could happen, based on historical trends to answer the question "What could we do?".
Predictive analytics uses the large amount and variety of data to build models that can find connections between seemingly unrelated variables. These models are produced through machine learning, which is the ability of computer systems to learn from data without explicit instructions.
For example, a machine-learning system can detect patterns of fraud from a database of credit-card transactions. The more data it processes, the better its predictions should be. However, in many cases, even strong correlations are not enough to guide effective action. Therefore, predictive analytics still depends on human judgment to decide and figure out what actions are most likely to work.
Prescriptive analytics tackles the problem of creating more causal models. Prescriptive analytics uses optimization techniques that rely on large data sets, rules on what we as a business will do in different situations, and mathematical models to answer the question "What should we do?".
Prescriptive algorithms can constantly update their data and improve their decision optimization. Since prescriptive models suggest the best course of action, human involvement becomes more crucial. The focus shifts from a purely analytical task to a whether or not accepting a suggested course of action.
Initiating, changing or maintaining a state or behaviour manually or with actuators: Act
The final stage of the Information-Value Loop is involves initiating, changing or maintaining a state or behaviour, be it manually or using actuators. Supported by information, these are value-driven actions, actions to create more value. In this stage, the information that was generated and analyzed in the previous stages is used to influence the physical world and achieve a desired outcome.
Manual intervention
 One way to perform actions is to use manual intervention, which means that the user decides what action to take based on the information they receive and then does it themselves. To put it plainly, in case of a system with water levels, the users close a water pipe themselves.
One way to perform actions is to use manual intervention, which means that the user decides what action to take based on the information they receive and then does it themselves. To put it plainly, in case of a system with water levels, the users close a water pipe themselves.
Manual intervention can be useful when the user wants to have more control over the situation, or when the information is not sufficient or reliable enough to automate the action. For example, a smart watch can provide information about the user's health and fitness, such as:
- Heart rate: the user can monitor their heart rate and decide whether to exercise more, rest, or seek medical attention.
- Calories burned: the user can track their calories burned and decide whether to eat more, less, or differently.
- Steps taken: the user can count their steps and decide whether to walk more, less, or differently.
Actuators
 Another way to perform actions is to use actuators, which are devices that can convert electrical signals into physical movements or effects. To put it plainly, the users press a button and a motor (the actuator) closes the water pipe.
Another way to perform actions is to use actuators, which are devices that can convert electrical signals into physical movements or effects. To put it plainly, the users press a button and a motor (the actuator) closes the water pipe.
Actuators can be used to control various aspects of the environment, such as:
- Lighting: a smart bulb can use an actuator to change the color or brightness of the light based on the user's input.
- Sound: a smart speaker can use an actuator to play music or respond to voice commands based on the information it processes from the cloud or the user's input.
- Motion: a smart door lock can use an actuator to lock or unlock the door based on the command it receives from the user's smartphone, or the cloud.
Automatic adjustments with machine-to-machine interfaces
 However, manual intervention can also have some drawbacks, such as human errors, biases, or delays. Therefore, some actions can be better performed by using automatic adjustments, which means that the system can adjust itself based on the information it receives, without requiring human input. To put it plainly, the system watches the water level by itself and a motor closes the water pipe if needed.
However, manual intervention can also have some drawbacks, such as human errors, biases, or delays. Therefore, some actions can be better performed by using automatic adjustments, which means that the system can adjust itself based on the information it receives, without requiring human input. To put it plainly, the system watches the water level by itself and a motor closes the water pipe if needed.
Machine-to-machine interfaces can replace reliably fallible human intervention with automated optimized processes. Insights into human cognitive biases are making prescriptions for action based on augmented intelligence more effective and reliable. For example:
- Temperature: a smart thermostat can use an actuator to adjust the heating or cooling system based on the information it receives from sensors and the user's saved preferences.
- Industrial power: a smart grid can use machine-to-machine interfaces to balance the supply and demand of electricity, based on the information it collects from sensors, smart meters, and other devices.
- Cars: A smart car can use machine-to-machine interfaces to communicate with other cars, traffic lights, and road signs, and adjust its speed, direction, and braking, based on the information it receives from these sources.
Conclusion: IoT 🤝 Value creation
Business, like many human activities, can be tempted by the allure of novelty. That is why we should view the Internet of Things with both curiosity and caution. IoT is a hot topic for many businesses and their leaders, who are eager to explore the potential of this new technology.
But they should not forget that the same old rule still applies: if something does not create value for a business, it is often not worth investing in. The IoT is not a magic bullet that can solve all problems; it is a tool that can be used wisely or poorly, depending on how well it aligns with the business goals and strategy.
In any case, to succeed with an IoT project businesses need to start every IoT project with a clear vision of the aspects in the information value loop for that project. They need to identify the sources and types of data they need and how to sense it, the ways they can communicate and aggregate it, the methods they can use to analyze it and turn it into information, and the actions they can take based on it. They also need to consider the costs and benefits of each stage, and the trade-offs and risks involved. By doing so, they can design and implement IoT solutions that create value for their business and their customers.
